Dark DAOs: The growing existential threat to a decentralized future In an age where the lines between truth, expertise, and democracy are increasingly blurred or twisted by those who have something to gain from that disorientation, we find these more nefarious elements of vote-buying on the rise in one area with clear consequences: voting systems for big decision-making bodies. Efforts are being led by Ethereum co-founder Vitalik Buterin and a group of researchers from Cornell University to help mitigate this risk. The forum takedown illustrates the flaws in the existing DAO paradigm, and it provides a few ideas on how to fix them.
What are Dark DAOs?
The DAOs, in one sense, work on a decentralized model where token holders are used to make decisions about things. Still, without a central oversight body, bribes might corrupt the voting process because bad actors could simply pay off token holders to vote, diminishing the DAO’s value.

To conduct a similar form of exploitation in the context of DAOs, smart contracts can be utilized to facilitate vote-buying behind closed doors—this is what dark DAOs do. Dark DAOs are a fundamental antithesis to one of the core tenants of decentralization: trust and transparency.
The Rise of Dark DAOs
Balancing central command with collective user input, DAOs distribute control throughout a non-hierarchical hierarchy in which decisions are made via majority voting among token holders. Though this is a transparent and very democratic way of working, it comes with its own flaws.
The idea of “Dark DAOs” is that bad actors can leverage these issues to pay token holders off for their votes in a way they want the vote cast. This also endangers the ability of a DAO to make decisions in an impartial and unbiased way, which presents an antithesis to decentralization.
Dark DAOs and Their Mechanism
These employ new tools and techniques in a way that results in inadequate defense mechanisms. And by preventing bribed voters from slithering back to the booth and changing their vote.
This is done through Trusted Execution Environments (TEEs) or some other cryptographic methods that reduce the ability of voters to use their keys only in certain ways, as for all intents and purposes, they determine votes.
The Bribery Threat in DAOs
However, the problem is that DAO voting systems are vulnerable to vote buying. This leads them to use a voting or consensus mechanism among token holders. Though this structure is meant to be democratic, it can easily be made less so. Penalization of proposals is not sufficient, and malicious actors can bribe the token holders fairly easily to get their proposal through.
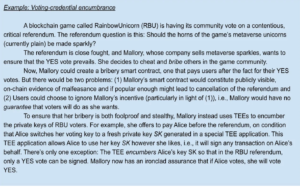
In his defense, Vitalik Buterin has been actively working to address these risks with some innovative cryptoeconomic solutions. An example of such a solution is the ‘Proof of Complete Knowledge’ (PoCK). This concept helps voters to have the correct knowledge and control of their voting keys, which significantly reduces the chances for attacks on vote manipulation.
Vitalik’s Warning
Also, Vitalik Buterin expressed concerns about the growing danger of bribery within DAOs. He notes that the more common DAOs become, the greater incentives will exist for adversarial players to attempt influencing votes. With these actors, smart contracts would automatically distribute bribes to token holders who vote in a specific way.
This not only undermines the fairness of the voting process but also affects DAO agency problems.
Proposals for DAO Solutions
Buterin and scientists have introduced the idea of Probative Find Out (POCK) to fight these issues. That system of cryptography ensures that voters must have actual control over their voting keys, so the risk of bribery is diminished. While it is early days for this research, the implications indicate a potential for creating much more secure and trusted DAO environments.

The team is looking into two primary ways to implement PoCK:
Trusted Execution Environments (TEEs): These are secure environments where the voting participant runs and votes in such a way that even while being remotely influenced by an attacker, it can guarantee that they will still be able to re-take control of governance because state variables are key.
Application-Specific Integrated Circuits (ASICs): The key is being available for the user by using ASICs and not misusing them in a TEE.
Proof of Complete Knowledge (PoCK)
PoCK is a mechanism, which is designed to ensure that the voter has full control of his or her keys and can use them without interference. This allows for a secure vote, but the voting is also completely anonymous, which is crucial in all decentralized systems.
Like, the influence from outside on those votes is limited to bribery as long as the term voter keeps its private key fully under control. Furthermore, PoCK can also be imposed by way of trusted execution environments (TEEs) or Application Specific Integrated Circuits (ASICs), an additional layer to secure the voting process.
The Future of DAO Governance
However, as a prototype, PoCK marks an important milestone in defending DAOs against bribery attacks. The continued evolution of DAOs will necessitate that these security features be integrated to support the integrity of decentralized governance. The work of Buterin and the gang illustrates why these vulnerabilities need to be addressed in advance if DAOs are going to have long-term success as a trustworthy form of organization.












